Introduction
Network security group (NSG) is just a group of Access Control List (ACL) rules that allow or deny network traffic to your VM instances in a Virtual Network. NSGs can be associated with the following.
- Virtual Machines – the rules get applied only to the Virtual Machine to which it is associated.
- Subnets – In this case, the rules get applied to all the Virtual Machines associated with the Subnet.
When a NSG is associated with a subnet, the ACL rules apply to all the VM instances in that subnet. In addition, traffic to an individual VM can be restricted further by associating a NSG directly to that VM.
In this article, we will learn how to create a NSG group and about the default Inbound and Outbound rules that gets created by default when you create an NSG.
let’s get started using Azure Management Portal.
Click on Network Security Group as shown below in the menu.

You will be taken to the Network Security Group blade where you would all the existing NSGs. As shown in the below screen capture, click on “Add” button.

You will be taken the following blade.
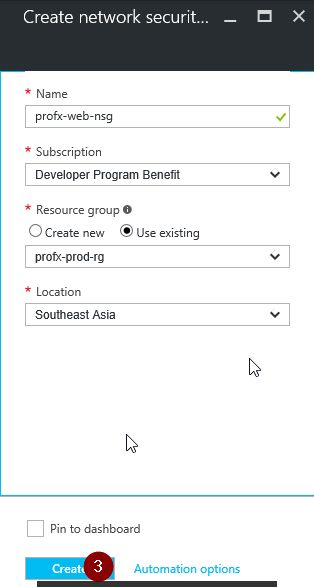
Provide a meaningful for the NSG. In your production scenarios with different environments and multiple servers, you might have to create multiple NSGs. Please be cautious in naming the NSGs. Select the Subscription, Resource Group and Location based on your requirements.
Now, clicking on “Create” button will create the NSG as shown in the below screen capture.
Below is the NSG’s Overview blade which provide the basic details of the NSG that we have just created.
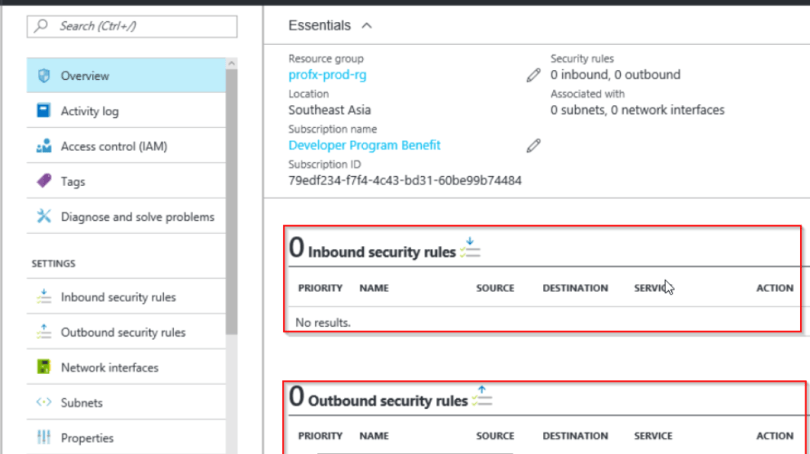
Let’s review the default Inbound Security and Outbound Security rules that get created automatically. Though the above screen capture shown the count of both type of rules is Zero (0), there are three Inbound and three outbound default rules that get created when you create a Network Security Groups.
Click on Inbound security rules or Outbound security rules box of the above screen capture to navigate to the respective Rules Blade as shown below.
Default Inbound Rules
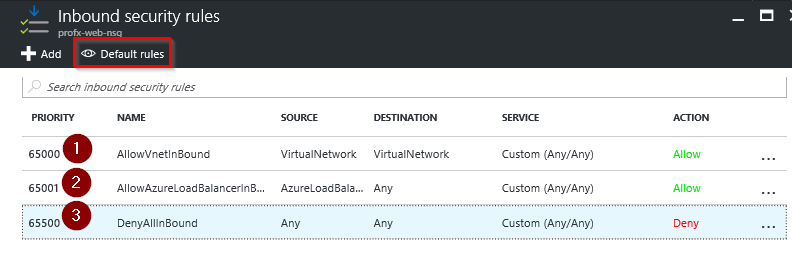
Below is the table that provide details about the default rules.
| Rule Name | Description |
| AllowVnetInBound | Allow Inbound traffic coming from any VM to any VM within the VNet |
| AllowAzureLoadBalancerInBound | Allow traffic from the default Load Balancer to any VM within the VNet |
| DenyAllInBound | Deny traffic from any external Source to any of the VMs |
Default Outbound Rules
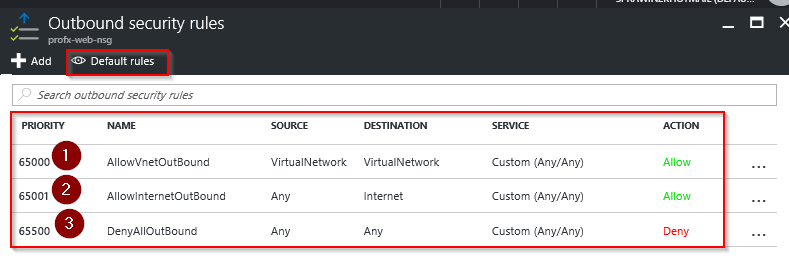
| Rule Name | Description |
| AllowVnetOutBound | Allow Outbound traffic going from any VM to any VM within VNet |
| AllowInternerOutBound | Allow Outbound traffic going to internet from any VM |
| DenyAllOutBound | Deny traffic from any Internal VM to any other system outside VNet |
Please note that you cannot delete these default rules.
Summary:
You have learned the following
- What is a Network Security Group?
- Where can we use Network Security Group
- Default Inbound and Outbound Rules that gets created when you create a Network Security Group.
Hi praveen, is there any script for knowing which ports are open for any vm’s or web apps in microsoft azure (ASMand ARM)
Please reply me if any script is had
LikeLike